Recently I had an requirement that I couldn’t find documented outside of the abstract; migrating a single private DNS zone to AWS’ hosted DNS service; Route 53 and conditionally forwarding queries for that zone from an existing Windows DNS infrastructure.
This isn’t something I expected to be broken down blow by blow in the AWS documentation but there are plenty of Windows DNS infrastructures out there in the wild and it was something I had expected someone to have blogged about by now or at least see it hacked together in a few StackOverflow posts.
Sadly I couldn’t find much, however with a little bit of understanding of the theory the process works really well so let’s look at how to get set up.
First of all, what’s the problem?
In our infrastructure, we have several private DNS zones managed within a Windows DNS infrastructure. If we want to migrate one of these zones to Route 53 for any reason we’re going to encounter an issue that our clients, who are receiving their IP configurations via DHCP will still be resolving all their DNS queries via our Windows DNS infrastructure.
We can’t just go pointing to Route 53 as it won’t know about any of our other zones, so we need to instruct our existing infrastructure to forward queries to our migrated zone.
What Are We Working With?
In this example we’ll be working with the following zones:
- madcaplaughs.co.uk
- madcaplaughs.dev
- madcaplaughs.testing
- madcaplaughs.staging
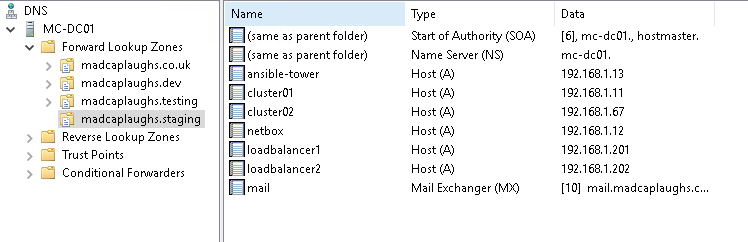
We will be migrating madcaplaughs.staging to Route 53, whilst the rest will remain in the Windows infrastructure.
In AWS, we already have the existing components in place:
- A VPC named mcvpc in region eu-west-2 with the address space 10.0.0.0/16.
- Two subnets named mcsubnet01 and mcsubnet02 split over two Availability Zones within the eu-west-2 region with the address spaces 10.0.1.0/24 and 10.0.2.0/24.
- A security group has been created named mc-staging-dns which allows ingress and egress for TCP port 53 (DNS Queries) from our on-premise networks only.
- A site-to-site VPN is active between the on-premise infrastructure and AWS.
Configuring a Private Zone in Route 53
The task here is quicker achieved via Terraform, however we’re trying to look at the steps involved so let’s use the GUI:
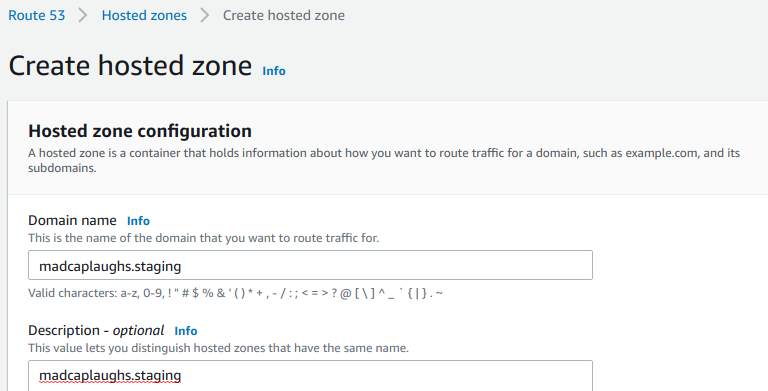
In the AWS Console we can create a new Hosted Zone if we browse to Route 53 > Hosted Zones > Create Hosted Zone:
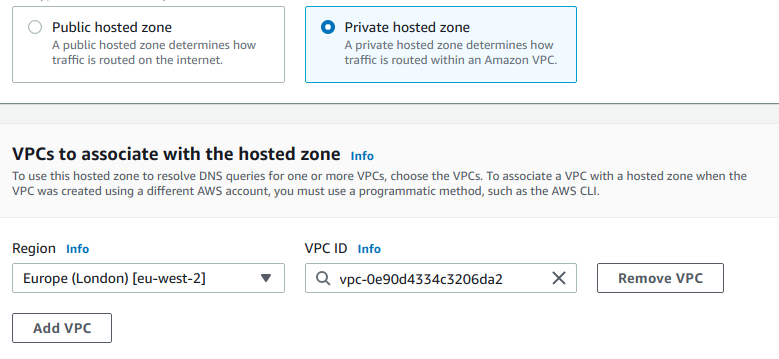
Below, select Private Hosted Zone and we’ll select our Region and VPC:
Finally, we can optionally set any Tags and create the Hosted Zone:
After a few seconds you can see that the Hosted Zone has created and that Nameserver and Start of Authority records have been created to use the Route 53 infrastructure. These cannot be removed or modified:
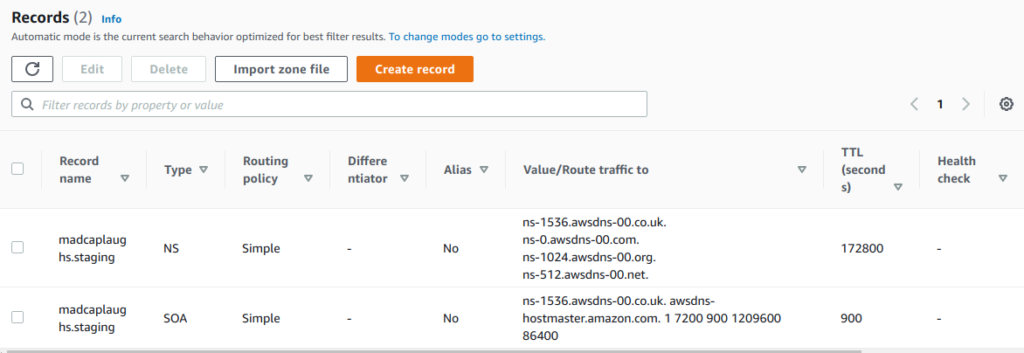
Your records can now be either manually created or imported in an RFC 1035 standard Zone File, in Windows the Zone Files are located by default at C:\Windows\System32\dns. I’ve written at length about performing DNS migrations here and the same rules apply when migrating a private zone so consider carefully when to cut over.
Configuring a Route 53 Resolver
So our zone is now stood up in Route 53 but we currently have no means to route any queries to our new Hosted Zone. This functionality is provided by the Route 53 Resolver service. For our needs we need to create an Resolver Inbound Endpoint which will accept queries from our on-premise network only (controlled using our already existing security group).
We can create a new Inbound Resolver by browsing to Route 53 > Resolver > Inbound Endpoint > Create Inbound Endpoint:
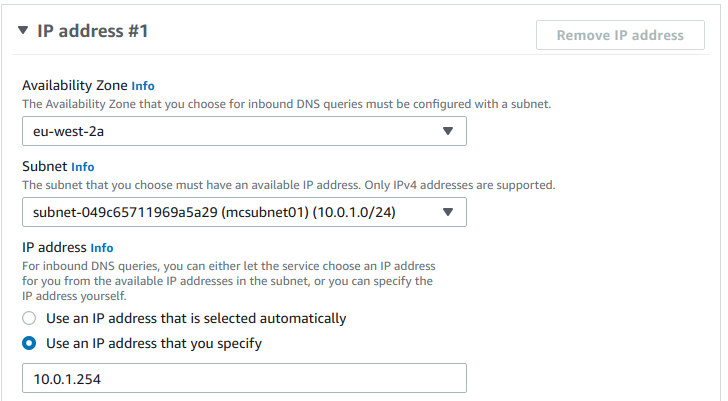
An Inbound Endpoint must have at least two IP addresses assigned to it to accept DNS queries, these IPs should be provided from subnets which are routable from our on-premise network. Our two subnets also need to be in two different availability zones:
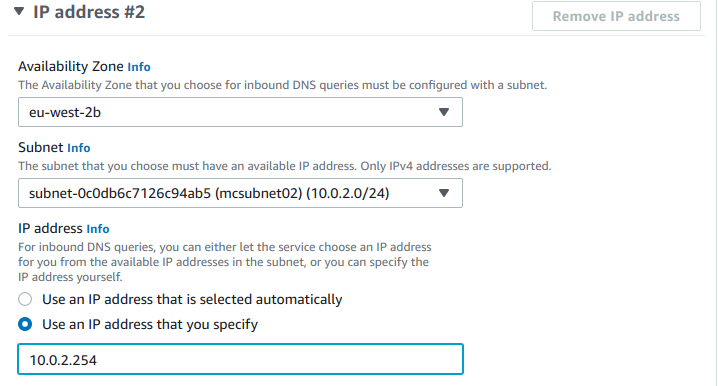
Finally, we can optionally add tags then Submit the creation:
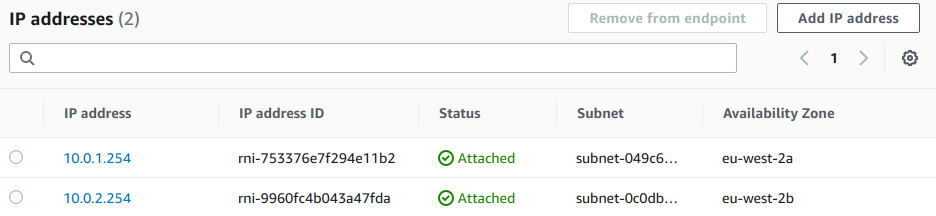
After a short while, the Inbound Resolver will be created, if we enter it’s configuration we can see that it is active and has the two IP addresses we provided:
Windows Server – Redirecting Queries
In order to complete the migration we first need to be sure that all records have been migrated to our Route 53 Hosted Zone, now in our Windows DNS console we can configure a new Conditional Forwarder:
The DNS Domain field should be completed with the FQDN of the domain we wish to forward to Route 53 and the IP addresses of the master servers list should be completed with the IP addresses used for our Resolver Inbound Endpoint.
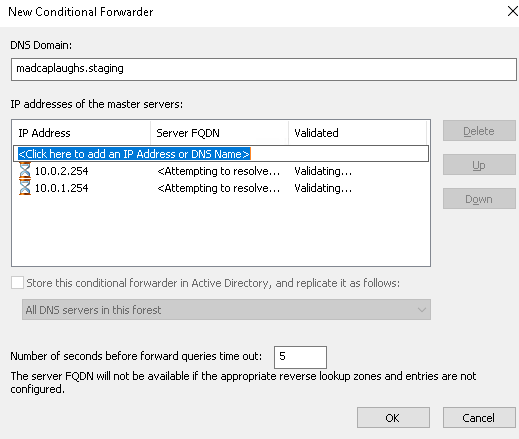
Click OK to create the Conditional Forwarder:
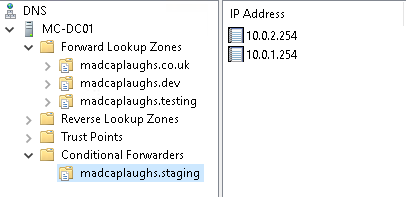
Finally, delete the zone from the on-premise DNS server, as you can see above it has been deleted and all queries for this zone will now to Route 53.
As a final measure, the DNS cache should be cleared using ipconfig:
ipconfig /flushdns
This process of configuring Conditional Forwarders, deleting the local zone and clearing the DNS cache should be repeated on all local DNS servers, once that’s done the zone will be fully migrated.